Setting up CUDA environment in Visual Studio 2017
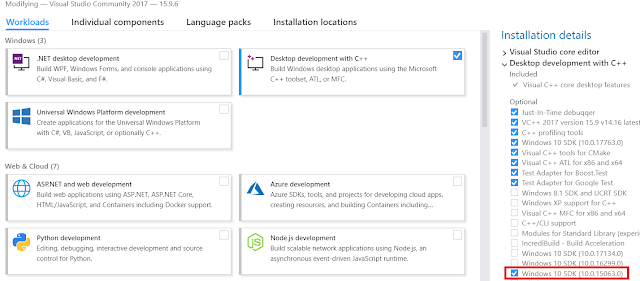
In this post I will briefly summarise two issues I came across while trying to setup the development environment for CUDA. CUDA is an environment that allows you to code the application with support of potent computational capabilities of your GPU-s. In my case, I wanted to utilise the power of NVIDIA GeForce 1050 Ti card. The idea of having this SDK is to facilitate a way for your application to distribute processing over parallel processing and multithreading. You can download CUDA SDK from https://developer.nvidia.com/cuda-downloads . (I used 10.1 version and Visual Studio 2017). Having downloaded and installed CUDA SDK (which takes some time), I tried to compile the deviceQuery utility - the example that, if compiled ok, would show you the attributes of your GPU. This is where the troubleshooting started. First of all, the compilation did not work due to missing Microsoft 10 SDK 10.0.15063.0 component. This can be easily installed by modifications in the Visual Studio. Go into t
