Investigating suspicious emails
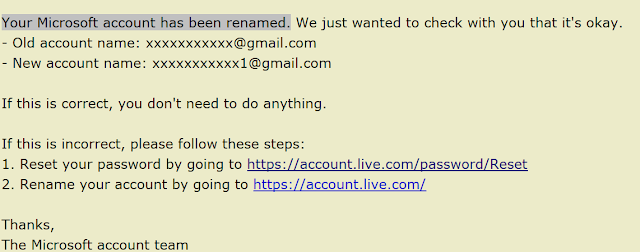
Recently I received an
email from Microsoft Account Protection informing me that my email account I
use as a secondary email for alerts in my online outlook has been renamed. As I
did not do any renaming of any accounts I use, I decided to conduct a little
investigation to find out the cause of this unexpected alert. The screenshot
below shows the english translation of that email (the original came in my own
language).
There were two objectives I intended to achieve
here :
a)
Find out if this is a hoax/phishing email or a legitimate Microsoft warning
b)
If it was a legitimate warning, who and why and when performed this change
as it surely wasn’t me.
The first task was to validate the email server
and the URL to determine if they both belong to Microsoft. I started the
analysis by checking the validity of the source SMTP server. The idea here was
to check its IP address, fully qualified domain name and SPF record.
The email header looks like a legitimate Microsoft
SMTP server, not the phishing campaign. Below are some additional checks run
against the SMTP IP address, domain and SPF record. It all looked good. We see
that the SPF record looks ok. SPF record is a DNS record that identifies
permitted servers to send email for a specific domain. (More info on https://ie.godaddy.com/help/add-an-spf-record-19218)
Received-SPF: pass
(google.com: domain of account-security-noreply@accountprotection.microsoft.com
designates 40.107.236.59 as permitted sender) client-ip=40.107.236.59;
Double-checking that SPF is indeed what email
header claims to be:
Double-check on the respective IP address to
domain translation and domain ownership was done consulting the whois database.
(More info on whois can be found on https://en.wikipedia.org/wiki/WHOIS). That established that the IP address of 40.107.236.59 is an IP address that
belongs to Microsoft and is also a SMTP server that sent the warning message.
The next step was checking the validity and
ownership of https://account.live.com
(note this URL in the initial email warning). Again, we apply the same strategy
– by combining DNS lookups with whois ownership the information is
cross-referenced and compared for any discrepancy.
Who owns account.live.com?
So, Microsoft seems to own the account.live.com
domain. Therefore, it is most likely not any phishing/malicious web site. At this stage I sent this email to Microsoft (to “abuse@microsoft.com”
and phish@office365.microsoft.com
) trying to figure out more details and context of this incident (is it
incident, at all?)
I decided to login to my legitimate outlook
account and have a look around- for example, establish if I can login at all,
if so, to check for alias, security setting, 2-factor authentication (my mobile
number) etc. The idea behind this step was to confirm I can successfully login.
Many times when the email account has been hijacked the legitimate user would
not be able to login (because the attacker changed the password) or would be
able to login but its phone number or forwarding email would be changed to
point to the attacker. The first step was to check if account alias was indeed
changed/added as the email warning indicated.
It turned out that all aliases were exactly as I
set them up.
Next step was checking the “Security settings” which
contained the email address I designated for receiving alerts. That was intact,
too.
I also checked “Recent activities” section that
shows timestamp and IP address of who recently accessed my account. Was able to
determine that both time and IP address of the access were mine.
At this stage, all looked ok.
I wish to clarify at this point some confusion
over the phishing campaigns which are so often outlined in many forums
discussing email incidents. First, the email source was coming from account-security-noreply@accountprotection.microsoft.com.
If you google this email address, you can indeed find the official Microsoft
email address is exactly that. However, bear in mind that the "From"
field can relatively easily be spoofed, so a valid email address is not
necessarily evidence of a “healthy” email. You need to analyse other data from
email header to confirm or deny that.
As the last step I decided to send an email to
the renamed email address from the above. This was done just to see if the
human on the other side may potentially respond that, for example, they were
changing anything with their account and mistyped mine at one stage which might
have triggered this alert.
Note that my legitimate email and the one which
it was allegedly renamed to, both end with the same surname, and start with the
same letter. Naturally, I assumed there is some living /real person behind it.
Unfortunately, I never received any reply to my inquiry from the “renamed”
email address. In the meantime, a response came from Microsoft Cyber Defense
Operations Center (CDOC). This response was asking me to forward the full email
for further investigation, which I happily did.
CDOC Case Management cdoccm@microsoft.com
As of now, I did not receive any further reply to
my incident, and at this stage I decided to terminate the investigation and
publish this article. The impression I am under and the bottom line of the
investigation sums up in the following – I am not very confident with the
(potential) incident support that Microsoft has demonstrated in this case.
Wonder what I’d do if this was some serious hijack of my email account.
This is a brief recapitulation of the situation:
a) the email seems to be coming from legitimate Microsoft
services (both URL and SMTP look like a legitimate Microsoft servers)
b) None of the setting in Outlook.com seems to
have changed (phone number, secondary email, alias, etc were all unaltered)
c) I still cannot reconstruct who,when and what
caused the account rename activity.
The Question that remains: how much can we trust/rely
on cloud providers once things go wrong?













Comments
Post a Comment