SMS scam and phishing web sites
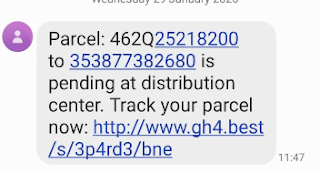
This post will describe the phishing campaign that target myself, among other individuals. In this review I will explain the reasoning (both technical and social) in assessing the validity of the sites, messages and the logic behind an attempt to obtain personal data from individuals. The whole story began when I received this SMS message on my mobile.
The SMS itself looks pretty much regular, even though the URL it directs you to is not exactly what I'd expect from a courier company. Not only it does not contain the names of either DHL, FastTrack, Post or any similar courier, but rather obscure name (gh4). Anyway, this was not my primary trigger - my primary trigger was an "every day life practice" - I could not remember I purchased anything! So, first thing firs, I contacted my wife to check if we're expecting anything. No. Ok, something's weird here...Let's investigate. I started with simple domain lookups to see who owns this web site.
Ok, not much here -just another cloud based service. The next step was to inspect the web content of this strange URL. I ran wget within isolated virtualised machine to see what comes back.
There is one URL reference in the file downloaded linking to the blogger.com - site used for various blogs, mostly hobbists, enthusiasts...Why would a parcel delivery be connected to sites that host blogs? I fired up my browser to the blogger's site.
Rather obscure, wouldn't you say - FR, SE, DK - does this mean there are sites variants for different countries, maybe different languages. I needed to see what these sites are, so let's start with the first one from the list, orig1TRK. Clicking this link opens the following page:
This is the parcel tracking site with the parcel ID as from the SMS. A strange source for my parcel, isn't it - blogger site? A couple of things here:
That makes sense because remember that the web sites from blogger.com indicated FR (France), DK (Denmark) and SE (Sweden) language options. My guess at this stage was that the perpetrator was from Denmark, although they may be using the fake info to misdirect the investigation. Further, when I browse b3.yocourse.com , this leads me to what it seems like fake yoga site. There is nothing on the webpage (yoga training) except the form for personal data. No contact, no address,no names of instructors, no description of Yoga classes…This is a suspicious lack of essential information for any decent web site, too.
Roughly a month after I received the original phishing SMS, I went to check the web reputation of the fake yoga site. It was accessed via corporate filtering engine.
Unfortunatelly, Fortiguard was among the rare ones that flagged this site as malicious. Very few online web reputation filters did the same(2 out of 35 that I checked). Many others showed nothing suspicious around this one.
Conclusion: the identified area/address in Denmark might be the perpetrator, assuming they control the payment interface. If not, the perpetrator may only be using couple of redirect URLs to point to a legitimate payment site.
However, based on the analysis it seems the whole b3.yocourse.com is being a phishing site and as such is owned most likely by the blogger above.
The SMS itself looks pretty much regular, even though the URL it directs you to is not exactly what I'd expect from a courier company. Not only it does not contain the names of either DHL, FastTrack, Post or any similar courier, but rather obscure name (gh4). Anyway, this was not my primary trigger - my primary trigger was an "every day life practice" - I could not remember I purchased anything! So, first thing firs, I contacted my wife to check if we're expecting anything. No. Ok, something's weird here...Let's investigate. I started with simple domain lookups to see who owns this web site.
Ok, not much here -just another cloud based service. The next step was to inspect the web content of this strange URL. I ran wget within isolated virtualised machine to see what comes back.
There is one URL reference in the file downloaded linking to the blogger.com - site used for various blogs, mostly hobbists, enthusiasts...Why would a parcel delivery be connected to sites that host blogs? I fired up my browser to the blogger's site.
Rather obscure, wouldn't you say - FR, SE, DK - does this mean there are sites variants for different countries, maybe different languages. I needed to see what these sites are, so let's start with the first one from the list, orig1TRK. Clicking this link opens the following page:
This is the parcel tracking site with the parcel ID as from the SMS. A strange source for my parcel, isn't it - blogger site? A couple of things here:
a)
You can change parcel ID to any other number, it will still show the same
delivery message. Doesn’t make sense.
b)
This is not a real tracking page (orig1 from the URL corresponds to the
orig1 from the URL published on the blog).
You land to the same web if you click the original http://www.gh4.best/s/3p4rd3/bne
from the SMS. As a matter of fact, HTTP 302 redirect request makes sure you land here. Orig1-ie.blogspot.com is the same server as
track-ie.blogspot.com (makes sense as both sites are just aliases running on
the same domain/machine)
I followed the game - clicked "Pay shipping" which leads me to yet another page, b3.yocourse.com
At this stage, I filled in the bogus details and clicked Next.
Note the phone number for questions : +4542907339. Two things that require further investigation here - b3.yocourse.com domain and the phone number. First, the domain lookup comes with this:
Who or what is WhoIsGuard Protected?
The phishing authors used WhoisGuard service for anonymisation
(the original SMS came with no identified phone number). That explains why there was no phone number displayed on the original SMS. Second artefact to inspect was the said phone number. Googling the number shows us that it's sourced from Denmark.
That makes sense because remember that the web sites from blogger.com indicated FR (France), DK (Denmark) and SE (Sweden) language options. My guess at this stage was that the perpetrator was from Denmark, although they may be using the fake info to misdirect the investigation. Further, when I browse b3.yocourse.com , this leads me to what it seems like fake yoga site. There is nothing on the webpage (yoga training) except the form for personal data. No contact, no address,no names of instructors, no description of Yoga classes…This is a suspicious lack of essential information for any decent web site, too.
Roughly a month after I received the original phishing SMS, I went to check the web reputation of the fake yoga site. It was accessed via corporate filtering engine.
Unfortunatelly, Fortiguard was among the rare ones that flagged this site as malicious. Very few online web reputation filters did the same(2 out of 35 that I checked). Many others showed nothing suspicious around this one.
Conclusion: the identified area/address in Denmark might be the perpetrator, assuming they control the payment interface. If not, the perpetrator may only be using couple of redirect URLs to point to a legitimate payment site.
However, based on the analysis it seems the whole b3.yocourse.com is being a phishing site and as such is owned most likely by the blogger above.














ReplyDeleteThanks for sharing valuable information!
Same Day Courier Delivery